Ap 9 Music Download Torrent
Get the awesome torrent downloader with no download speed or download size limits. Now downloading torrents to your phone is easy. From the team that invented the BitTorrent torrent protocol and uTorrent, the BitTorrent torrent app for Android is a beautifully simple way to discover, download, and play media, anywhere. Mar 3, 2019 - Yes, you can still get music for free on your phone. No, it's not illegal. Tune in and turn on to our best Android apps for downloading free music.
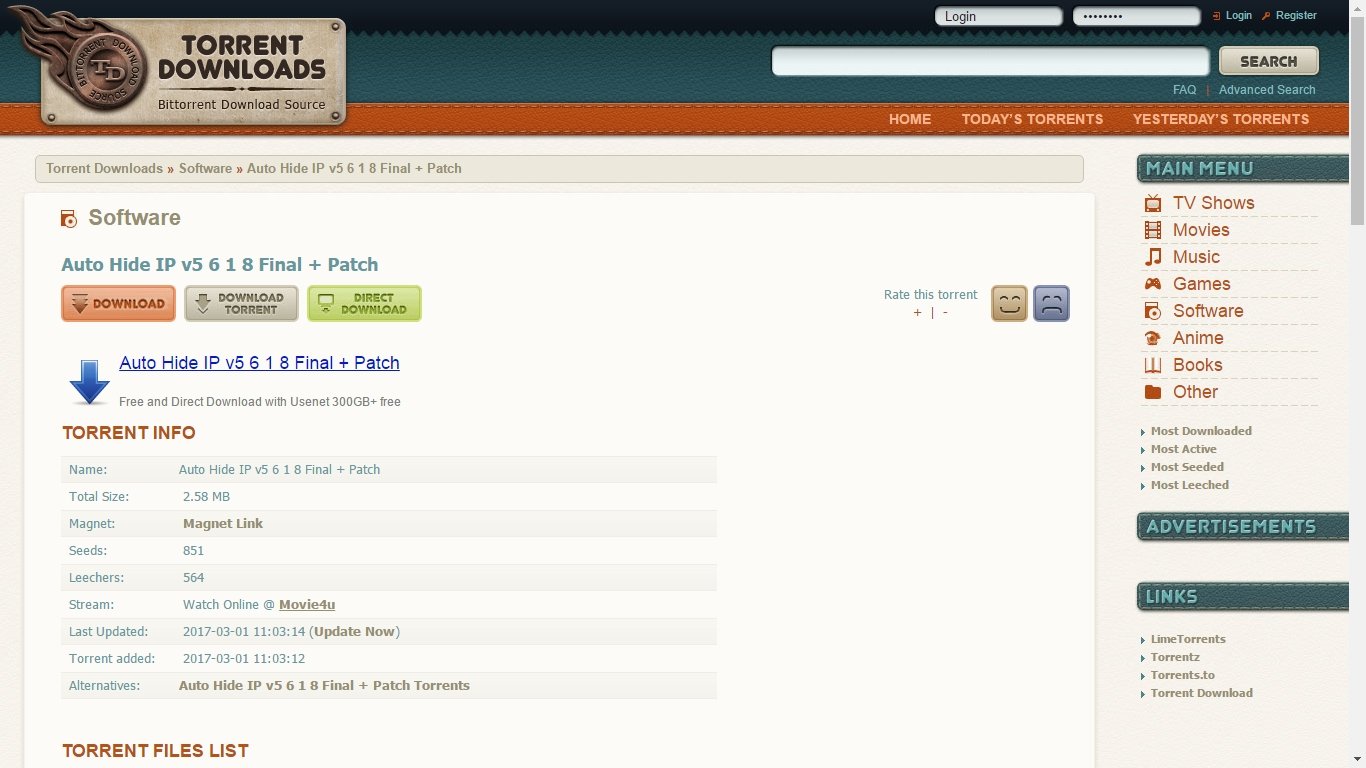
The top torrent sites currently include old favorites like The Pirate Bay, as well as very popular torrent sites like RARBG, 1337X, Torlock, YTS.ag, TorrentDownloads, and LimeTorrents.
That said, we know that the best torrent site is always the one that has the high-quality torrent you're after, and with the most seeders, so a large and thorough list of torrent sites, like those in the list below the torrents that are the best of the best, is always a welcome resource to find.
We don't condone illegal sharing of copyrighted files. Please see our full disclaimer and warning for new torrent users at the bottom of the page.
Tips for New Torrent Users
If you're new to torrents, we have two resources that will help you get started in torrenting.
- Torrent File Sharing: A Beginner's Guide: Learn how BitTorrent file sharing works, what a torrent file is, how to protect yourself, and how to get to the movies and music you're after in the safest and efficient way possible.
- How to Spot Fake Torrents: Fake torrents are a big problem and not one a newcomer might assume is something she or he has to worry about. This article contains lots of torrent site searching tips to keep you out of harm's way.
Find torrents and download them directly to your phone or tablet, with the official µTorrent® App (uTorrent App) for Android. Brought to you by the team that.
Also, be sure you're running fully updated anti-malware software before you visit any of these sites, and try one of the Best VPN Service Providers that can help keep your torrent activity, and other browsing, private and secure. Also, if you're new to torrents, don't forget that you'll need a torrent client to get these files.
All torrent sites below are working unless otherwise noted, at least as of the last update to this page. Let us know (feedback@lifewire.com) if we need to adjust a listing.
The Top Torrent Sites
These seven sites made the top of the list. They're not the only torrent sites out there, but they are among the best.
This torrent site is a classic, and one of the most popular on the web. TPB has been around in one incarnation or another for a long time and the torrents here are, and have always been, trusted.
Icons on each download help users quickly see if a seeder is trusted or a VIP which helps to ensure safe downloads.
TPB occasionally moves around. If you're still experiencing issues reaching TPB, try these listings on the ProxyBay. It's possible you'll find another way into the site.
This torrent site is for movie enthusiasts. It's full of quality, high-resolution video torrents.
Top 10 lists help users find the most popular movies on the site, and a detail page for the download includes a variety of information from the size of the file and the date it was added to actor information, and the number of seeders and leechers for the download.
At RARBG, it’s about quality, not quantity.
If you're after older or more obscure torrents, 1337X might be for you. Their torrent database isn't nearly as large as some others, but it might have just what you're after. The front page is regularly updated with current and popular information about torrents, torrenting, and categories of interest.
The level of advertising you’ll encounter on this site is frustrating. Links often require two clicks..one to bring up an ad (in a separate window) and one to actually access the information you want. However, once you get passed the advertising, the search result pages contain lots of useful information.
This is the 'no fake torrent' site you've been waiting for. The site actually pays its users $1 per fake torrent they find, and claims to have more than 5 million verified torrents.
You’ll find current and popular files to download in movies, anime, software, games, and music, as well as other categories, and a Top 100 list lets you know what’s most popular with the most seeders and peers.
Focusing exclusively on movies, YTS.am (or YTS.ag) has an easy-to-use layout and a wide variety of titles both old and new. The torrents themselves are known to be easy on bandwidth, which will make those with data caps happy.
YTS.am is the unofficial successor to the now-defunct YTS/YIFY group, which closed its virtual doors in 2015. The current site has a massive user base, too, which helps the bittorrent protocol work more efficiently.
We love the super straightforward torrent detail page at TorrentDownloads. That would be reason enough to give this one a try but the big database and high quality of torrents make it a great choice.
Users can find current torrents in a variety of categories. The ability to rate files and leave comments on files helps to reduce the number of fake files found on the site. An Advanced Search option also allows users to narrow the field of possible returns by category, provider, and status.
You don't want to miss this site in your torrent search. Users report the size of their database is impressive and the frequency of legitimate torrents is enough to keep them coming back.
It’s easy to quickly determine whether a torrent is worth downloading. Internal lists show the date added, size, seeder and leechers, as well as a health meter for each file. The information page for each download also provides additional information about the file.
Other Torrent Search Sites
There are way more than just seven torrent sites out there, of course. We’ve compiled the following list, just in case you want to explore beyond the ones above.
The advertisements on many of these sites are often of the NSFW variety. You should use caution when accessing these sites from public computers or with children present.
- Popcorn Time: Popcorn Time is a site dedicated to streaming movies for free, so in the strictest of terms, it's not a torrent download site. However, if you don't mind watching movies on your PC, you'll find plenty of options here, and you can watch them as often as you like.
- Torrentz2: This is like a super torrent index, searching for torrents across dozens of other torrent sites. You can see the complete list in their Sites in our index page.
- ETTV Torrents: This is a good, active site that includes television episodes. The site search functionality is good enough and the site has a nice, clean design.
- Torrent Galaxy: A decent database of torrents, good search features, and a clean website design make Torrent Galaxy another site you want to include in your search.
- KAT: This is the official torrent site! Don't be tricked by mirrors of the same name.
- EZTV: You won't find every torrent you're after here, but users say the quality of the torrents you do find is consistently good. This site, like others, can go down sometimes; a little bit of patience will likely see it back up.
- Torrents.me: This meta torrent site isn't too special among all the others but we love the amazing dashboard on their home page. If you're a data nerd and a torrent fan, you'll appreciate what they've done.
- Monova: A nice, clean design is reason enough to spend time on this torrent site. Advertising can be an issue at times but if you can get over that, it's a great torrent site.
- Toorgle: This is another meta torrent search engine, pulling the databases in from over 450 torrent sites into one place.
- Seedpeer: With a sizable database of torrents, Seedpeer is and always has been a great place to search. The interface isn't as nice as some others, but it's still a very usable site.
- TorrentFunk: This is a pretty popular torrent site, in no small part due to its verified status indication, as well as user reviews.
- Zooqle: This is another torrent site you don't want to skip in your search. Users love the size of their database and the frequency of legitimate torrents.
- BitTorrent Database: With a huge database and pretty clean interface that's devoid of advertisements, it's no wonder this multi-million strong collection of torrents is one we frequently hear about.
- YourBittorrent: The clean interface is a big reason to try this torrent searcher..especially if you're new to BitTorrent.
- 7tor: 7tor appears to be a Russian website, though the greatest traffic to this site comes from Pakistan. However, the site is minimally maintained, and only available if enough users donate to support the monthly hosting for the site. It does appear that torrents are still being added to the site, so you may be able to find obscure titles here.
- rutracker: Another site that appears to be Russian, this site is currently active and appears to have current torrents available. Rutracker also offers distribution awards, a hall of fame, and more.
- Pirateiro: This English-language site, offers a variety of downloads, including current and older files. A word cloud at the top of the home page lets users know what the most popular searches on the site are.
- Nyaa: Nyaa is a Chinese-language site that also seems to have some English- and other languages available in downloads. You can easily track seeders and peers on the downloads you find here, as well as the ability to comment on files.
- ArenaBG: This Bulgarian site was restricted in Bulgaria. It’s now based in Frisco, Texas. The site is fairly easy to use, once you translate it to your preferred language, and offers both current downloads and older files.
Disclaimer & Torrent Legal Warning
Lifewire does not condone illegal sharing of copyrighted material. While P2P file sharing technology itself is completely legal, many of the files traded through P2P are indeed copyrighted. Uploading these copyrighted files puts you at risk of a civil lawsuit in the USA, Canada, Australia, and the UK, at a minimum.
Lawsuits can be targeted at individual users or groups of users. These P2P civil lawsuits are very real and, whether or not they are successful, they are often an extreme financial and emotional burden on the defendants.
Additionally, your Internet Service Provider may choose to release a history of your download and upload activity to potential copyright plaintiffs. In general, the more data you download and upload, the more risk you have of being sued by copyright protection groups.
Torrent poisoning is intentionally sharing corrupt data or data with misleading file names using the BitTorrent protocol. This practice of uploading fake torrents is sometimes carried out by anti-infringement organisations as an attempt to prevent the peer-to-peer (P2P) sharing of copyrighted content, and to gather the IP addresses of downloaders.[1]
- 1Methods of attack
- 2Barriers to torrent poisoning
Methods of attack[edit]
Decoy insertion[edit]
Decoy insertion (or content pollution) is a method by which corrupted versions of a particular file are inserted into the network. This deters users from finding an uncorrupted version and also increases distribution of the corrupted file.[2] A malicious user pollutes the file by converting it into another format that is indistinguishable from uncorrupted files (e.g. it may have similar or same metadata). In order to entice users to download the decoys, malicious users may make the corrupted file available via high bandwidth connections.[3] This method consumes a large amount of computing resources since the malicious server must respond to a large quantity of requests.[4] As a result, queries return principally corrupted copies such as a blank file or executable files infected with a virus.[5]. There were known cases when a company had created a special version of a game and published it on file sharing services advertising it as cracked, having undocumented hidden functionality, making it impossible to win this variant of the game.
Index poisoning[edit]
This method targets the index found in P2P file sharing systems. The index allows users to locate the IP addresses of desired content. Thus, this method of attack makes searching difficult for network users. The attacker inserts a large amount of invalid information into the index to prevent users from finding the correct resource.[3] Invalid information could include random content identifiers or fake IP addresses and port numbers.[5] When a user attempts to download the corrupted content, the server will fail to establish a connection due to the large volume of invalid information. Users will then waste time trying to establish a connection with bogus users thus increasing the average time it takes to download the file.[3] The index poisoning attack requires less bandwidth and server resources than decoy insertion. Furthermore, the attacker does not have to transfer files nor respond to requests. For this reason, index poisoning requires less effort than other methods of attack.[4]
Spoofing[edit]
Some companies that disrupt P2P file sharing on behalf of content providers create their own software in order to launch attacks. MediaDefender has written their own program which directs users to non-existent locations via bogus search results. As users typically select one of the top five search results only, this method requires users to persevere beyond their initial failed attempts to locate the desired file.[6] The idea is that many users will simply give up their search through frustration.
Interdiction[edit]
This method of attack prevents distributors from serving users and thus slows P2P file sharing. The attacker’s servers constantly connect to the desired file, which floods the provider’s upstream bandwidth and prevents other users from downloading the file.[6]
Selective content poisoning[edit]
Selective content poisoning (also known as proactive or discriminatory content poisoning) attempts to detect copyright violators while allowing legitimate users to continue to enjoy the service provided by an open P2P network. The protocol identifies a peer with its endpoint address while the file index format is changed to incorporate a digital signature. A peer authentication protocol can then establish the legitimacy of a peer when she downloads and uploads files. Using identity based signatures, the system enables each peer to identify infringing users without the need for communication with a central authority. The protocol then sends poisoned chunks to these detected users requesting a copyright protected file only. If all legitimate users simply deny download requests from known infringers, the latter can usually accumulate clean chunks from colluders (paid peers who share content with others without authorization). However, this method of content poisoning forces illegitimate users to discard even clean chunks, prolonging their download time.[7]
Voluntary Collective Licensing and the Open Music Model are theoretical systems where users pay a subscription fee for access to a file-sharing network, and are able to legally download and distribute copyright content.[8] Selective content poisoning could potentially be used here to limit access to legitimate and subscribed users, by providing poisoned content to non-subscribed users who attempt to illegitimately use the network.[9]
Eclipse attack[edit]
The eclipse attack (also known as routing-table poisoning), instead of poisoning the network, targets requesting peers directly. In this attack, the attacker takes over the peer’s routing table so that they are unable to communicate with any other peer except the attacker. As the attacker replicates the whole network for the targeted peer, they can manipulate them in a number of ways. For example, the attacker can specify which search results are returned. The attacker can also modify file comments. The peer’s requests can also be directed back into the network by the attacker and can also be modified. It also checks data randomly for any errors found in that.[10]
Uncooperative-peer attack[edit]
In this attack, the attacker joins the targeted swarm and establishes connections with many peers. However, the attacker never provides any chunks (authentic or otherwise) to the peers. A common version of this attack is the 'chatty peer' attack. The attacker establishes connection with targeted peers via the required handshake message, followed by a message advertising that they have a number of available chunks. Not only does the attacker never provide any chunks, they also repeatedly resend the handshake and message. These attacks prevent downloads as, essentially, the peer wastes time dealing with the attacker, instead of downloading chunks from others.[11]
Barriers to torrent poisoning[edit]
There are several reasons why content providers and copyright holders may not choose torrent poisoning as a method for guarding their content. First, before injecting decoys, content providers have to normally monitor the BitTorrent network for signs that their content is being illegally shared (this includes watching for variations of files and files in compressed formats).
Berner the big pescado download. Jan 26, 2018 - Name: Berner – The Big Pescado Genre: Rap| Hip-Hop Year: 2018. Label: Bern One Entertainment Featuring: The Game, Pusha T, Conway,.
This process can be expensive and time-consuming. As a result, most poisoning is only continued for the first few months following a leak or release.[6] Second, it is also unlikely that torrent poisoning can be successful in disrupting every illegal download.
Instead, the aim of content providers is to make illegal downloads statistically less likely to be clean and complete, in the hope that users will be discouraged from illegally downloading copyright material. Content providers and copyright holders may decide that the financial outlay is not worth the end result of their efforts.
Countermeasures[edit]
The methods of attack described above are not particularly effective on their own, as for each measure effective countermeasures have evolved. These measures must be combined in order to have a significant impact on illegal peer-to-peer filesharing using BitTorrent protocols and Torrent files.
- BitTorrent is highly resistant to content poisoning (as opposed to index poisoning), as it is able to verify individual file chunks.[12] Overall, BitTorrent is one of the most resistant P2P filesharing methods to poisoning.[7]
- On private tracker websites, where all posted torrents can be traced to a particular member, poisoned torrents can be quickly labeled and deleted and the poster can be banned, preventing further introduction of poisoned torrents by that user.
- Public torrent tracker sites have enabled the ability to report if a torrent has been poisoned (or is fake or malicious in any way). Thus torrent files shared by public trackers can have similar levels of quality assurance as Private Tracker websites.
- Tracker technology (as well as BitTorrent client programs) has improved over time, and many kinds of spoofing that were possible in the past are no longer possible.
- BitTorrent was once an exclusively TCP-IP protocol, but this is no longer true. Use of UDP, with the uTP protocol has made TCP Man in the Middle attacks more difficult to nearly impossible.
- Public or Private tracker websites have selectively switched over to using HTTPS for the distribution of their web text and image content. By using HTTPS for the website content (versus tracker communications) many poisoning techniques are rendered impossible.
Legal issues[edit]
In September 2004, Altnet sued the Recording Industry Association of America, Overpeer, Loudeye, MediaSentry and others, claiming that their spoofing services violated Altnet's patent for a file identification method called TrueNames.[13][14]
In 2005 the Finnish anti-infringement organisation Viralg claimed that their software, which uses a similar approach to spoofing, could be used to bring an end to illegal P2P file sharing.[13] The firm offered 'total blocking of peer 2 peer sharing for your intellectual property' and claimed that its 'patented virtual algorithm blocks out all illegal swapping of your data'.[15] as well as claiming that their approach was 99% effective.[13] Despite these claims, the algorithm has not yet been tested with BitTorrent.[16] A group of Finnish musicians requested an investigation into the company, arguing that their software was effectively a virus and was in violation of Finnish law. The investigation was declined by Finnish police, and later by the Finnish parliamentary ombudsman.[17]
In some jurisdictions, there were concerns that content providers and copyright holders engaging in poisoning activities may be held liable for damages to users' computers. In the USA in 2002, Representative Howard Berman proposed the Peer To Peer Piracy Prevention Act, which would have granted immunity to copyright holders for taking steps to prevent the illegal distribution of their content (i.e. poisoning activities) on P2P networks, as long as they did not go as far as to harm the files stored on a P2P user's computer.[18][19] However, the bill died later in 2002 when the Congressional Term ended and has not been reintroduced.[20]
High-profile cases[edit]
In 2005, it was reported that HBO was poisoning torrents of its show Rome by providing chunks of garbage data to users.[21] HBO were also reported to have sent cease-and-desist letters to the Internet Service Providers (ISPs) of downloaders they believe have illegally downloaded episodes of The Sopranos.
Although not targeted specifically at BitTorrent, Madonna'sAmerican Life album was an early example of content poisoning. Before the release of the album, tracks that appeared to be of similar length and file size to the real album tracks were leaked by the singer's record label. The tracks featured only a clip of Madonna saying 'What the fuck do you think you're doing?' followed by minutes of silence.[22][23]
Similarly, the band Barenaked Ladies released a number of tracks online in 2000 that appeared to be legitimate copies of tracks from the band's latest album. Each file contained a short sample of the song, followed by a clip of a band member saying, 'Although you thought you were downloading our new single, what you were actually downloading is an advertisement for our new album.”[24]
After an unauthorized copy of Michael Moore’s movie Sicko was uploaded online, it became a hit on P2P websites such as Pirate Bay. MediaDefender was hired to poison torrents using decoy insertion.[25]
In an example of Internet vigilantism, anti-infringement vigilantes have been known to create viruses that are distributed exclusively via P2P networks, and are designed to attack mp3s and other music files stored on a user's PC. The Nopir-B worm, which originated in France, poses as a DVD copying program and deletes all the mp3 files on a user's computer, regardless of whether or not they were legally obtained.[13][26]
On 19 October 2007 Associated Press (AP) released information accusing the broadband service provider Comcast of 'hindering' P2P file sharing traffic.[27] Tests conducted by AP have shown that Comcast hindered the uploading of complete files to BitTorrent. The Federal Communications Commission conducted public hearings in response to the allegations. Comcast argued that it was regulating network traffic to enable reasonable downloading times for the majority of users.[28] On 21 August 2008 the FCC issued an order which stated that Comcast's network management was unreasonable and that Comcast must terminate the use of its discriminatory network management by the end of the year. Comcast complied with the order and appealed. On 6 June 2010, the District Court of Appeals for the Columbia vacated the FCC order in Comcast Corp. v. FCC.
Music Torrent
See also[edit]
References[edit]
- ^Cuevas, R. et al. (2010) Is Content Publishing in BitTorrent Altruistic or Profit-Driven?. Proceedings of the 6th International Conference on emerging Networking EXperiments and Technologies (ACM CoNEXT 2010). Philadelphia, USA. 30 November - 3 December 2010.
- ^Luo et al (2009). An Effective Early Warning Scheme against Pollution Dissemination for Bittorrent. In: Global Telecommunications Conference, 2009. Honolulu, 30 November – 4 December. New Jersey: IEEE. pp. 1 -7.
- ^ abcKong, J. et al (2010). A Study of Pollution on Bittorrent. In: The 2nd International Conference on Computer and Automation Engineering. Singapore, 26–28 February 2010. New Jersey: IEEE. pp. 118-122.
- ^ abKong, J. et al (2010) The Evaluation of Index Poisoning in BitTorrent. In: D. Wen. et al (eds). Proceedings of the Second International Conference on Communication Software and Networks. Singapore. 26–28 February 2010. New Jersey: IEEE. pp. 382-386.
- ^ abSantos et al (2010). Choking Polluters in Bittorrent File Sharing Communities. Network Operations and Management Symposium (NOMS) 2010. Osaka, 19–23 April 2010. New Jersey: IEEE. pp. 559-566.
- ^ abcAnderson, N. (2007). Peer-to-peer poisoners: A tour of MediaDefender. Ars Technica. Retrieved 2011-03-30.
- ^ abLou, X. and Hwang, K. (2009) Collusive Piracy Prevention in P2P Content Delivery Networks. IEEE Transactions on Computers. 58 (7) pp. 970-983.
- ^von Lohmann, F. (2008) A Better Way Forward: Voluntary Collective Licensing of Music File Sharing. Electronic Frontier Foundation. Retrieved 2011-04-22.
- ^Lou, X., Hwang, K. and Zhou, R. (2007) Integrated Copyright Protection in Peer-to-Peer Networks. In: 27th International Conference on Distributed Computing Systems Workshops (ICDCSW'07). Toronto, Canada. 22–29 June 2007. p. 28
- ^Locher, T. et al. (2010) Poisoning the Kad Network. In: Kant, K. et al (eds). Distributed Computing and Networking. Heidelberg: Springer. pp. 195-206.
- ^Dhungel, P. et al. (2008) A Measurement Study of Attacks On Bittorrent Leechers. In: Proceedings of the 7th International Conference on Peer-To-Peer Systems (IPTPS ’08). Tampa Bay, Florida. 25–26 February 2008. Berkeley: USENIX. p.7.
- ^Lou, X. & Hwang, K. (2006). Adaptive Content Poisoning To Prevent Illegal File Distribution in P2P Networks Retrieved 2011-03-21.
- ^ abcdBruno, A. (2005) Viralg Touts P2P Solution. Billboard. 117 (20). p. 10. Retrieved 2011-04-23
- ^Cowley, S. (2004) Altnet Fights Back, Sues RIAA. PCWorld. Retrieved 2011-04-23.
- ^Viralg homepage. Retrieved 2011-04-23
- ^Ingram, M. (2005) Slyck News - Claim to End 99% of Illegal Trading. Slyck. Retrieved 2011-04-23.
- ^Viralg
- ^Berman, H.L. (2002) The Truth About the Peer to Peer Piracy Prevention Act: Why Copyright Owner Self-Help Must Be Part Of The P2P Piracy Solution. FindLaw. Retrieved 2001-04-23.
- ^Garrity, B. (2003) Spoofing Continues To Grow. Billboard. 115 (20). p. 7. Retrieved 2011-04-23.
- ^33 Sw. U. L. Rev. 397 (2003-2004). The Piracy Prevention Bill, H.R. 5211: The Second Generation's Answer to Copyright Infringement over Peer-to-Peer Networks. Pesta, Kristine
- ^Torkington, N. (2005). HBO Attacking BitTorrent. O'Reilly Radar. Retrieved 2011-03-31
- ^BBC News (2003). Madonna swears at music pirates. Retrieved 2011-03-30.
- ^The Smoking Gun (2003). Hacked: Madonna's Web Site Defaced. Retrieved 2011-03-30.
- ^Murray, B.H. (2004) Defending the brand: aggressive strategies for protecting your brand in the online arena. AMACOM Books. p. 119. Retrieved 2011-04-23.
- ^Brodesser-Akner, C. (2007) After pirates steal 'Sicko,' Weinsteins deploy decoys; people hunting for new Moore movie might find advertising instead. Advertising Age. 18 June 2007. p. 3. Retrieved 25 April 2011.
- ^Sophos. (2005) Nopir worm fights pirates by wiping MP3 music files, Sophos reports. retrieved 2011-04-23.
- ^Associated Press. (2007) Consumer groups ask FCC to fine Comcast . msnbc.com. Retrieved 25 April 2011.
- ^Roth, D. (2009) The dark lord of broadband. Wired. 17 (2) p.54.